
New research from IOActive has found that “blindly” trusting the encryption of the widely adopted device protocol can lead to DDoS, sending of false data and other cyber attacks.
The LoRaWAN protocol has become standard in the world of industrial IoT because of its support for low-power wireless devices over long distances and its end-to-end encryption technology. However, bad implementations and security flaws make the protocol a real blind spot in the fraught world of IoT security, as LoRaWAN is easily susceptible to threats that could cause widespread disruption and even destruction if it’s not implemented correctly, IOActive researchers have found.
LoRaWAN, or Long Range Wide Area Networking protocol, allows low-powered devices to communicate with internet-connected applications over long-range wireless connections. Users and developers of IoT devices in smart cities, industrial IoT, smart homes, smart utilities, vehicle tracking and healthcare have widely embraced the protocol because of the false sense of security its encryption provides, according to a report by IOActive released Tuesday.
In reality, LoRaWAN encryption keys are easily obtained by a savvy hacker to conduct DDoS attacks and send false data to networks, researchers have found. Moreover, it’s currently impossible for organizations to know if a LoRaWAN network is under attack or if an encryption key has been compromised, making defending such attacks perilous, they said.
Indeed, it’s the perception that LoRaWAN is inherently secure that makes it so dangerous, noted Cesar Cerrudo, CTO at IOActive, the lead author of the report, “LoRaWAN networks susceptible to hacking: Common cyber security problems, how to detect and prevent them.”
“The LoRaWAN protocol is advertised as having ‘built-in encryption’ making it ‘secure by default,'” he wrote in the report. “As a result, users are blindly trusting LoRaWAN networks and not paying attention to cyber security; however, implementation issues and weaknesses can make these networks easy to hack.”
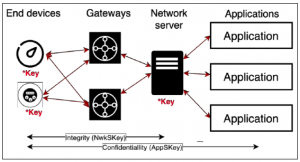
The LoRaWAN protocol defines two layers of security: one at the network level and another at the application level, researchers described in the report.
The network-level security ensures the authenticity of the device in the network, providing integrity between the device and the network server, they wrote. The application-layer security is responsible for confidentiality with end-to-end encryption between the device and the application server, preventing third parties from accessing the application data being transmitted.
Each layer of protection depends on the security of two encryption keys–the Network Session Key (NwkSKey) and the Application Session Key (AppSKey), both of which are 128 bits long. These keys are “the source of the network’s only security mechanism, encryption,” and thus, once cracked, basically give hackers an open invitation to the devices and networks being protected by them, researchers noted.
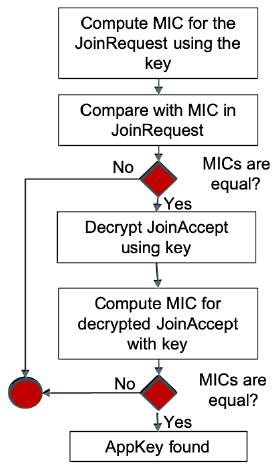
The problem with this architecture is that the keys are surprisingly easy to obtain for people who aren’t supposed to have access to the network or devices, researchers found, who outline numerous ways bad actors can obtain the keys to LoRaWAN networks.
These methods include: using reverse engineering to “sniff” keys from devices; obtaining keys from device tags displaying the code administrators forgot to remove before a device was placed in its final location; stealing source code for a device from open-source repositories or vendors websites; guessing keys that show lack of sufficient randomness; or cracking a network with default or weak credentials or other security vulnerabilities and stealing the keys from these servers.
Other ways hackers can obtain encryption keys to LoRaWAN networks include by compromising the system of the device manufacturer responsible for installing the firmware with device keys; hacking the devices or computers of technicians responsible for deploying devices where the keys might be stored; obtaining the keys from flash drives or emails of clients or device manufacturers where they were disclosed and shared; breaching a service provider who had keys stored in their backups or databases; or obtaining an AppKey in a dictionary or brute-force attack, researchers wrote.
Once bad actors obtain the encryption keys for a LoRaWAN network, they have a number of attack options available “to compromise the confidentiality and integrity of the data flowing to and from connected devices,” IOActive researchers wrote. These include conducting DDoS attacks that can disrupt communications between connected devices and the network server so companies can’t receive any data.
Attackers also can use the keys to intercept communications and replace these with false data, such as fake sensor and meter readings. In this way, bad actors can hide malicious activity or cause industrial equipment to damage itself, which could not just cause company disruption but potentially destruction of infrastructure or facilities if this occurs at a power plant or in the location of other critical infrastructure, researchers said.
The potential for these attacks is especially troubling since companies have no way to currently detect them, researchers noted. To help solve this issue, IOActive has released a LoRaWAN Auditing Framework on GitHub to help security administrators to audit and pentest the security of their LoRaWAN implementations.
Above all, researchers recommend that those implementing LoRaWAN networks make protecting security keys a top priority in the security of their implementations. Easy ways to do this include replacing keys provided by vendors with random keys; using different keys for different devices; auditing the root keys used to detect weak keys; and making sure service providers follow security best practices and have a secure infrastructure, they said.
"easy" - Google News
January 28, 2020 at 07:02PM
https://ift.tt/3aQBgUE
LoRaWAN Encryption Keys Easy to Crack, Jeopardizing Security of IoT Networks - Threatpost
"easy" - Google News
https://ift.tt/38z63U6
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini















0 Response to "LoRaWAN Encryption Keys Easy to Crack, Jeopardizing Security of IoT Networks - Threatpost"
Post a Comment